Cybersecurity training can be an overwhelmingly annoying issue for everyone. Unfortunately, it’s a must. Understanding the reasons behind this reluctance can help organizations tailor their training programs to be more engaging and effective. In this month’s newsletters, we go into four common reasons why employees might harbor disdain for cybersecurity training.
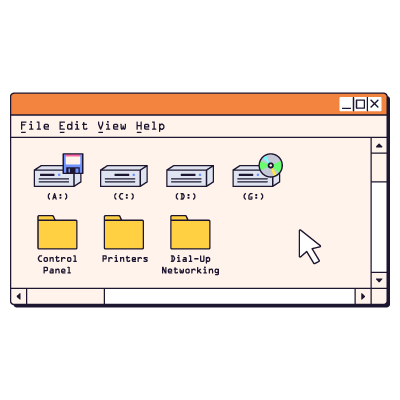
When discussing technology, the term “drives” is frequently used. This term encompasses various types that a computer may utilize in its daily operations within your business. This month, our aim is to explain the functions of these drives and underscore the importance of knowing their locations and significance.
Your business’ IT security effectiveness relies heavily on how well your technology works. With this in mind, educating your staff on their responsibility to safeguard your business’ digital assets is important. Let’s explore the key priorities businesses need to consider to establish a robust security training platform that works to protect those assets.
Picture this scenario: while going about your daily routine, an email lands in your inbox, purportedly from a cybersecurity company. The alarming claim is that you’ve become the target of a hacking attack. Despite lacking IT expertise and being unfamiliar with your security agency’s protocols, you trust the message and promptly respond. Little do you know, the email is a cleverly disguised cyberthreat, and you find yourself ensnared in their trap.
Every year on March 31st, World Backup Day serves as a dedicated occasion to emphasize the crucial role of regular data backups in ensuring the seamless continuity of information. While this awareness day effectively underscores a fundamental best practice, we staunchly advocate for an ongoing commitment to continually maintaining and protecting backups, extending beyond the confines of a singular day.
Imagine this scenario: amidst your daily routine, an email arrives in your inbox, seemingly from a cybersecurity company. The alarming assertion is that you’ve become the target of a hacking attack. Despite lacking IT expertise and being unfamiliar with your security agency’s procedures, you trust the message and respond promptly. Unbeknownst to you, the email is a shrewdly disguised cyberthreat, ensnaring you in their trap.
The web is filled with all types of content, and depending on where you live, it can be regulated by a myriad of organizations from all sections of society. From internationally recognized trade organizations to governments to industry regulators, there are a lot of moving parts in data regulation as it now stands. That leads to people wanting more control over data and censorship. Let’s take a look at cyber censorship and how it’s a bigger issue than you might think.
Ensuring seamless communication across all levels of your organization by addressing potential antiquated technologies and refining your strategy commensurate with your needs is more important today than ever before. It isn’t without challenges. To assist you, we lay out the following tips on how to improve your organization’s communications.
Recycling your technology is something that you may not put too much thought into, but the facts are that a lot of the technology we use can be really harmful to the environment if it isn’t recycled properly. This month, we are going to go into what happens to your old tech and how having a plan for recycling your old tech can help.
World Backup Day, observed on March 31st annually, serves as a designated occasion to underscore the critical importance of regular data backups for ensuring data continuity. Although this day effectively highlights a fundamental best practice, we firmly advocate for a continuous commitment to maintaining and safeguarding backups rather than confining such awareness to a single day.